Researchers at Microsoft have discovered a North Korean hacker group, called ‘Moonstone Sleet,’ that is carrying out both spying and financial cyberattacks. This group uses a variety of attack methods to target organizations in the aerospace, education, and software industries, as well as individual software developers.
Initially, Microsoft observed that Moonstone Sleet had a lot in common with another well-known North Korean hacking group, Diamond Sleet. They shared malware, like the Comebacker Trojan, and used similar infrastructure and techniques, such as spreading malicious software through social media. However, Moonstone Sleet has since developed its own unique infrastructure and a somewhat unpredictable identity.
Unlike other North Korean hacker groups that typically focus on either spying or stealing money, Moonstone Sleet does both. This is reflected in their diverse tactics, which include fake job offers, custom ransomware, and even a fully functional fake video game.
“Moonstone Sleet’s ability to mix traditional cybercriminal methods with those of nation-state actors is particularly alarming,” says Adam Gavish, co-founder and CEO of DoControl. “Their wide-ranging strategies — from creating fake companies to deliver custom ransomware to using compromised tools for direct infiltration — make defending against them more complicated.”
Moonstone Sleet’s Various Tactics
One notable tactic is their use of trusted platforms like LinkedIn, Telegram, and freelancing websites to target victims. By taking advantage of the trust people have in these platforms, they can more easily trick victims into engaging with malicious content.
To make their attacks more convincing, Moonstone Sleet often pretends to be legitimate companies. For example, from January to April this year, the group pretended to be a software development company called “StarGlow Ventures.” With a professional-looking website, fake employees, and social media accounts, StarGlow Ventures targeted many organizations in the software and education sectors, sending phishing emails that praised the recipients and proposed collaborations on upcoming projects.
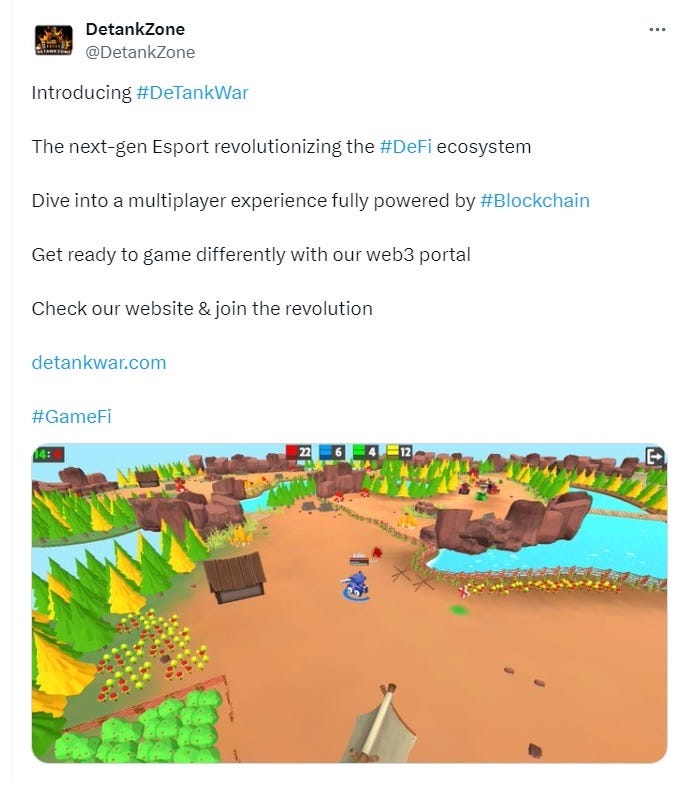
In another scheme, the group created a fake company named C.C. Waterfall to spread a particularly clever trick. Since February, emails from C.C. Waterfall have been inviting victims to download a video game called “DeTankWar,” also known as DeFiTankWar, DeTankZone, or TankWarsZone. This game is marketed as a community-driven, play-to-earn tank combat game, complete with dedicated websites and social media accounts for its fake personas.
Surprisingly, DeTankWar is a fully functional, though basic, video game. However, when users launch the game, it also installs malicious software that can probe the victim’s computer, collect data, and allow the attackers to execute commands on the victim’s system.
Whack-a-Mole Cyber Defense
Moonstone Sleet employs a variety of deceptive tactics, such as creating fake companies and video games, to carry out their cyberattacks. The group even tries to get its members hired for remote tech jobs with legitimate companies. They spread malicious npm packages through LinkedIn and freelancing websites and use their own ransomware, called FakePenny, accompanied by a ransom note copied from NotPetya, to demand millions of dollars in Bitcoin.
Given these diverse tactics and tools, Adam Gavish advises that “defenders must adopt a multi-layered security approach.” This means using a combination of endpoint protection, network monitoring, and threat hunting to detect and respond to unusual activities early on. Microsoft’s blog echoes this sentiment, recommending network and tamper protections, as well as endpoint detection and response (EDR), among other measures to strengthen cyber defenses.
“Ultimately,” Gavish adds, “the dynamic nature of threats like Moonstone Sleet requires a comprehensive and adaptable cybersecurity strategy — one that balances technical defenses with strategic intelligence and continuous vigilance.”